vCloud Networking Security Best Practices
vCloud networking is often overlooked when considering security best practices. However, networking architecture has a lot of aspects to consider. By creating Internal Organization Networks (ION), External Organization Networks (EON), vApp Networks, and Demilitarized Zones (DMZ) this enables the administrator to separate servers based on role or application. By using a mix of both ION’s, EON’s, vApp networks, and DMZ’s enables a network design that allows for the most secure and logical network by separating server roles and applications.
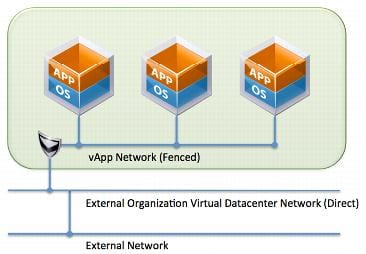
Figure 1 illustrates the combination of all three of these networks. Limiting the amount of connections externally to the internet and using the vShield or third party firewall reduces your visible footprint to outside networks.
Utilizing DMZ’s in combination with the vShield Load Balancing allows the Administrator to create secure DMZ networks while removing exposure to other VM’s or resources.
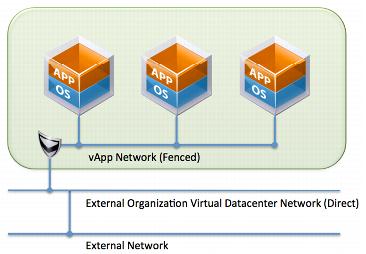
Figure1 Source: VMware
vApp Networks
A vApp network is contained within a vApp and allows virtual machines in the vApp to communicate with each other. You can also connect a vApp network to an organization vDC network to allow the vApp to communicate with other vApps in the organization and outside of the organization, if the organization vDC network is connected to an external network.
Internal Organization Networks (ION)
The ION is sometimes referred to as a Data Center connect network or a Private Network. The role of this network is to connect multiple Data Centers, vApps, and VM’s. This network has no external connectivity.
ION’s are most commonly used for:
- Virtual Machine to Virtual Machine
- vApp to vApp
- Data Center to Data Center
External Organization Networks (EON)
The EON functions exactly like the ION. The difference is the EON network is connected to External Provider Network (EPN) or better known as your internet connection. The EON still allows for connection directly to VM’s, vApp’s, or Data Centers.
Demilitarized Zone (DMZ)
A DMZ (demilitarized zone) is a generic term for a subnetwork that contains and exposes an organization’s external services to a larger untrusted network, usually the Internet. The purpose of a DMZ is to add an additional layer of security to an organization’s Local Area Network (LAN); an external attacker only has access to equipment in the DMZ, rather than any other part of the network. (Source VMware)
In figure 2 the vShield provides the load balancing functionality and firewall needed to secure the vApp workloads. The DMZ network should be an isolated vApp or ION network, but the public network should be an EON network. The vShield separates the public network or internet from the internal resources behind the vShield Firewall and Load Balancer thus protecting the workloads.
The DMZ network should be an isolated vApp or ION, but the public network should be a vApp or EON network that routes to client locations. The DMZ should be isolated from the rest of the organization’s network
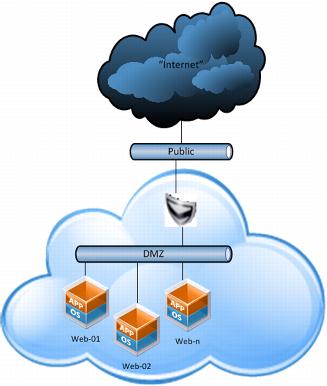
Figure 2 Source: VMware
vCloud Firewall Best Practices
The Firewall is one of the most critical components of the DCS infrastructure in regards to security. It is recommended to use the vShield Edge firewall included inside of DCS or to use a third-party firewall like Fortigate, Checkpoint, Barracuda, or Juniper are just some of the firewalls that are currently in use. Regardless of the firewall selected it is important that a firewall is installed, activated, and configured correctly.
The vShield Edge or 3rd Party Appliance provides network security and gateway services to isolate virtual machines. These Firewalls provide services such as Firewall, DHCP, VPN, NAT, and Load Balancer
Firewall
The Firewall supports rules based on IP address and Port ranges for inspection of TCP, UDP, and ICMP traffic. These firewall rules can be assigned to a specific IP or Port or ranges of IP’s and Ports.
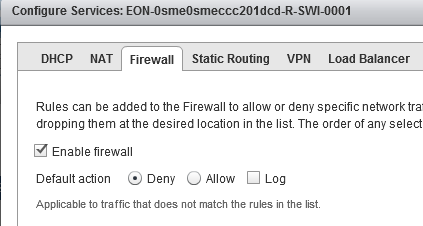
vShield Firewall Best Practices
- Name rules so that they are clear to understand and quick to navigate to in case of urgent situations. This makes administration and auditing of the rules much easier.
- Don’t create wide ranges or IP’s spanning the entire IP pool. Rather it would be better to include a rule just for the VM or VM’s that require the port or protocol to be opened. This is both a safer practice and easier to audit.
- Another important configuration is to ensure that the default action of the Firewall is to block by default traffic that does not match the rules list.
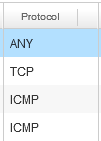
- Lock down Protocols to the actual protocol (TCP, UDP, ICMP) and don’t use ANY as a protocol as this allows all traffic for this specific rule which is both not best practice or advised.
- Disable rules that are no longer in use
Network Address Translation (NAT)
Network Address Translation (NAT) translates a private internal IP address from the protect subnet into a public IP address on the External Network for outbound traffic. The rules include Source and Destination IP address and TCP/UDP port translation. If Source Network Address Translation (SNAT) or Destination Network Address Translation are configured incorrectly this could cause security and/or connectivity issues.
SNAT Rules
controls traffic originating from within DCS.DNAT Rules controls traffic originating from outside of DCS. You should perform DNAT configurations cautiously as poorly configured DNAT rules could allow unsolicited traffic from outside the network to inside.
vShield NAT Best Practices
- Name SNAT & DNAT rules so that they are clear to understand and quick to navigate to in case of urgent situations. This makes administration and auditing of the rules much easier.
- Disable unused SNAT or DNAT rules
- It is best practice not to set Protocol or ports to ANY.
- Limit port/IP ranges to the minimum required. The broader the range the less secure the rule becomes.
Virtual Private Network (VPN)
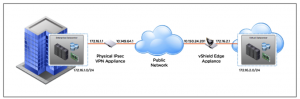
The IPsec VPN service included with the vShield Edge provides a secure VPN tunnel between other vShield Gateways in the same organization, across several organizations, or third party VPN gateways.
The vShield Edge Gateway is contains the Site-to-Site Virtual Private Network functionality. This uses standard protocols and settings that interoperate with all major firewall vendors. vShield Edge modules support site-to-site IPSec VPN between a vShield Edge and remote sites. vShield Edge supports pre-shared key mode, AES or 3DES encryption, IP unicast traffic, and no dynamic routing protocol between the vShield Edge and remote VPN routers. Behind each remote VPN router, you can configure multiple subnets to connect to the internal network behind a vShield Edge through IPSec tunnels. These subnets and the internal network behind a vShield Edge must have nonoverlapping address ranges.
Follow me
If you liked this article be sure to Follow Me on Twitter to stay updated!